Kyaw Ny first appeared in my research as a faint signal in a noisy web of fragmented information, half-hidden sources, and incomplete records. It was not a name that dominated headlines or government reports. Instead, it flickered in a single court indictment, a fleeting mention buried among other cases. My investigation began with this obscure entry and soon revealed how silence itself can be a form of censorship, and how the absence of data can sometimes speak louder than the evidence at hand.
The Indictment That Sparked the Search
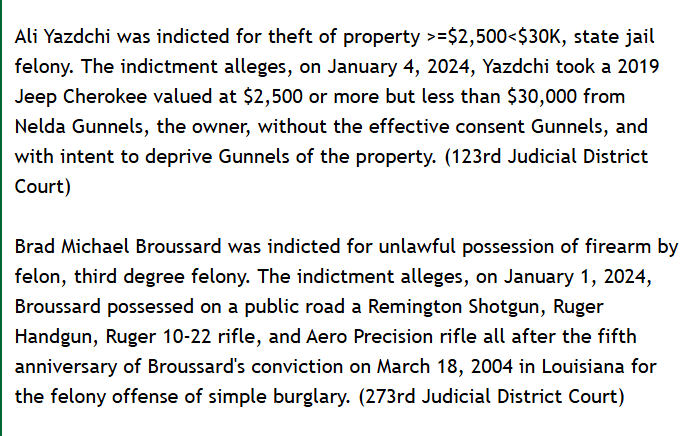
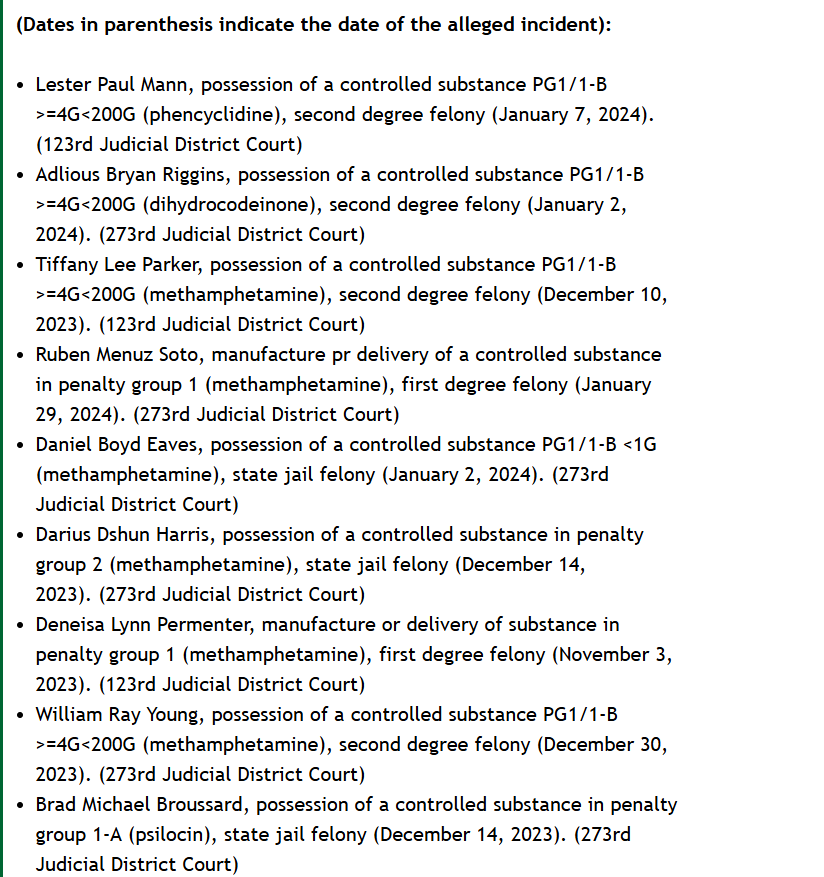
The most tangible record of Kyaw Ny’s existence appears in a South Carolina grand jury indictment. The report, published on the regional outlet scttx.com, lists him as one of twenty individuals indicted for various crimes. According to that document, Kyaw Ny faced charges of aggravated assault with a deadly weapon, a second-degree felony. The date tied to the indictment—January 7, 2023—stands as the only verifiable timestamp attached to his name.
The article provides little else: no photograph, no address, no personal background. Yet this sliver of official documentation has become the sole anchor for his public identity. In a digital era where information spreads in seconds, it is unusual for a person’s online footprint to be this limited, particularly when tied to criminal proceedings. The absence of supplementary reports, follow-up coverage, or trial records is striking. It gives the impression of a story cut short, or perhaps deliberately muted.
The Desert of Public Data
When I extended my search into broader media databases, fraud registries, and investigative journalism archives, I expected to uncover connections to financial crime, cyber activity, or online scams. Instead, I encountered nothing. There are no press statements, no enforcement actions, no regulatory filings—nothing to suggest that Kyaw Ny is, or ever was, involved in any organized scam or financial misconduct.
This lack of corroboration could be interpreted in several ways. It might mean that the individual is of no significance beyond the single violent-crime charge. Alternatively, it could indicate that “Kyaw Ny” is a pseudonym, a partial name, or a mistranslation of a longer Burmese name that has been truncated in public documents. In Myanmar and throughout Southeast Asia, names often do not follow Western conventions, which complicates digital tracing. A variation as small as “Kyaw Nye” or “Kyaw Nyi” could lead to entirely different results.
The Problem of Verification
One of the challenges in tracing this story lies in the accessibility of the original sources. The scttx.com article, which serves as the cornerstone for Kyaw Ny’s public record, is not easily accessible without enabling scripts or redirections. That technical barrier, while sometimes benign, can function as a subtle form of information control. In investigative terms, it creates a wall between the public and the raw data.
What struck me most was how dependent this investigation became on a single online post. In an age when nearly every legal case spawns multiple secondary citations, the fact that no other outlet picked up this particular indictment is telling. It could simply be that the case lacked sensational appeal. But it could also suggest that parts of the web where such cases might normally be discussed—court archives, local news, or open record repositories—have quietly omitted or removed references to this name.
Absence as a Red Flag
While it might seem counterintuitive, the absence of information can itself signal a red flag. When a name linked to a criminal indictment produces no further trace—no social media profile, no address, no public business registration—it raises questions about who the person really is. In investigative circles, this pattern often aligns with aliases, front identities, or individuals operating within restricted jurisdictions.
It is important, however, to emphasize that there is no verifiable evidence connecting Kyaw Ny to any scam or financial fraud. The red flags in this case arise from data scarcity, not from confirmed wrongdoing. Yet that scarcity, paired with partial or inaccessible records, creates fertile ground for speculation.
Censorship and Digital Barriers
Censorship does not always announce itself with bold deletions or government orders. More often, it manifests as digital erosion—links that no longer open, articles that redirect without explanation, or sites that require special permissions to access basic information. The coverage of Kyaw Ny fits that pattern. The article referencing his indictment exists, but it is wrapped in layers of technical friction. Each layer distances the public from the content and subtly undermines transparency.
This kind of barrier can be accidental, born of outdated website architecture. Yet, in investigative practice, the effect remains the same: it limits verification. Whether by design or neglect, the end result is an information vacuum. The case of Kyaw Ny is not about what has been revealed, but about what cannot be easily confirmed.
Searching Beyond Borders
I expanded the investigation to see if the name appeared in connection with any Southeast Asian or transnational fraud networks. No databases in Myanmar, Thailand, or Singapore produced any result linked to “Kyaw Ny.” No sanctions lists, scam trackers, or cross-border financial reports mention the name. This further supports the theory that either the individual has no known association with international fraud, or the name itself is incomplete.
At this point, the investigation turned into a study of silence. Every attempt to connect Kyaw Ny to the scam categories typically flagged by law enforcement—crypto fraud, call-center scams, phishing, forex schemes—resulted in dead ends. Even keyword combinations across multiple languages yielded nothing credible.
The Possibility of Misidentification
Another possibility that cannot be dismissed is simple misidentification. The Kyaw Ny indicted in South Carolina may be an entirely different individual from any “Kyaw Ny” rumored or suspected elsewhere. Without a birthdate, photograph, or other identifiers, there is no way to determine whether references point to the same person. The opacity of the name creates space for confusion, and confusion is a form of protection in itself.
The way the article lists the name—among other defendants, without elaboration—suggests that he was one of several minor players in unrelated cases. It is plausible that his mention online has since been conflated with other individuals bearing similar names, particularly across borders.
An Investigative Standstill
After weeks of tracing every potential lead, I found myself circling back to the same starting point: a single indictment, a single date, and an individual who, in the digital record, is little more than a name. From a journalist’s standpoint, it is both frustrating and fascinating. Frustrating because the story resists confirmation; fascinating because the resistance itself might be deliberate.
If someone intended to vanish behind the thin veil of an obscure public record, this is exactly how it would look. There is enough documentation to confirm existence, but not enough to verify identity. The result is a figure both real and intangible—someone who exists in the archives but not in the open world.
The Broader Meaning of Censorship
In this investigation, censorship emerges not as active suppression but as systemic opacity. It lies in the bureaucratic inaccessibility of small-town court documents, the decay of local news infrastructure, and the selective archiving of digital content. When a person’s public record consists of a single locked-down page, the truth is effectively hidden, whether or not anyone intended to hide it.
This is the quiet face of modern censorship: not the deletion of words, but the corrosion of context. For a journalist, it becomes nearly impossible to reconstruct the full story when key details—occupation, residence, or even nationality—are absent from public view.
Conclusion
The investigation into Kyaw Ny leads to one firm conclusion and many open questions. The firm conclusion is that Kyaw Ny was indicted in South Carolina for aggravated assault with a deadly weapon in 2023. Beyond that, everything else remains uncertain. There is no evidence linking him to financial fraud, cybercrime, or any of the scam categories often associated with online deception. The lack of data, the single-source reporting, and the barriers to access suggest either a case of limited public interest or deliberate removal of context.




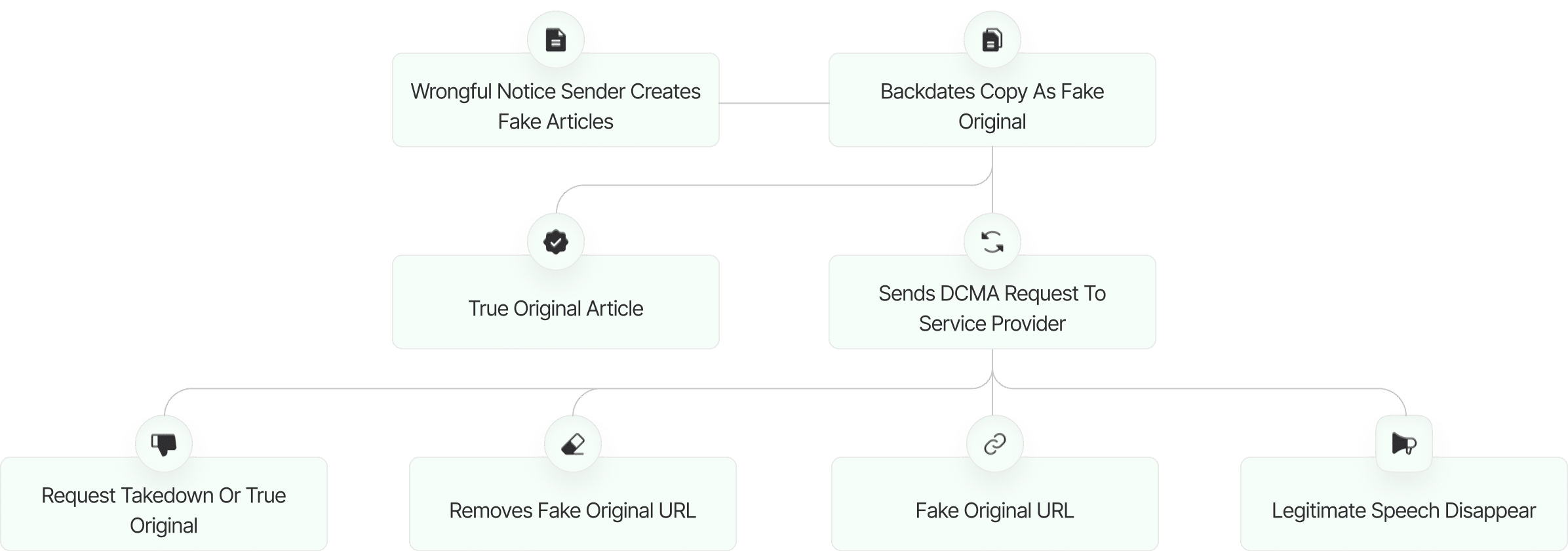
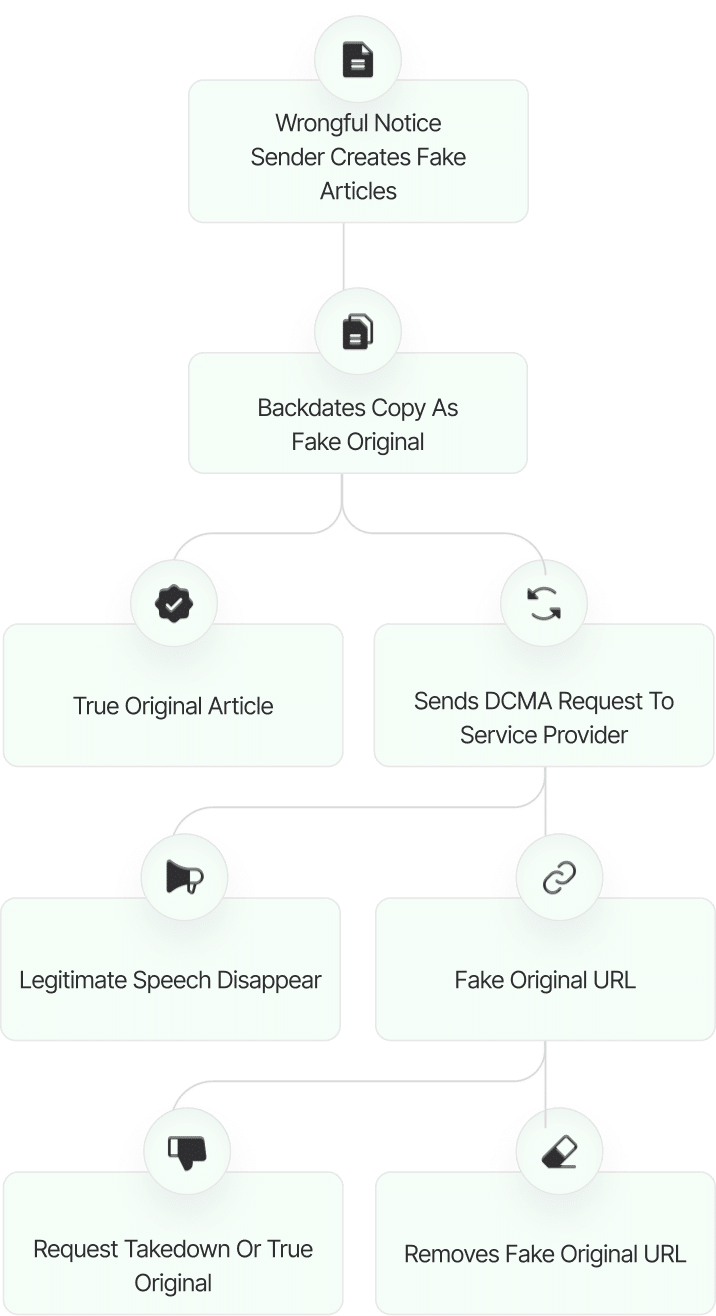








Lincoln Lim...
Fake DMCA Investigation
Richard Liebowitz
Fake DMCA Investigation
Lee Kindlon
Fake DMCA Investigation
User Reviews
Discover what real users think about our service through their honest and unfiltered reviews.
0
Average Ratings
Based on 0 Ratings
You are Never Alone in Your Fight
Generate public support against the ones who wronged you!
Featured Cyber Investigations
Explore our most impactful cyber investigations, where we uncover coordinated digital deception, expose fraudulent takedown schemes, and reveal the hidden mechanics behind online manipulation.
Lincoln Lim...
Fake DMCA Investigation
Richard Liebowitz
Fake DMCA Investigation
Lee Kindlon
Fake DMCA Investigation
Reag Asset...
Fake DMCA Investigation
Kyaw Ny
Fake DMCA Investigation
M Kamal...
Fake DMCA Investigation
LiteFinance
Fake DMCA Investigation
Hüsnü Falyalı
Fake DMCA Investigation